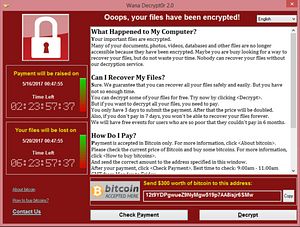
Since the first infection of WannaCry in Europe on Friday at 15:24 CST, an unknown (presumably) non-state actor has leveraged stolen NSA malware to hold hundreds of thousands of computers in over 150 countries hostage and demand ransom. On Monday, as workers across Asia signed into their computers after the weekend, the ransomware spread further. The victims include universities, gas stations, stores hospitals, government agencies, and movie theaters in China, Russia, Japan, South Korea, and Singapore, among numerous other Asian states. After the initial rapid growth of WannaCry, a private cyber security researcher had found a ‘kill switch’ and the infection rate declined. However, Kaspersky Lab’s Global Research and Analysis warned of “several new variants” of WannaCry resistant to the kill switch emerging in the last 24 hours that were “manually patched by unknown entities and have not been created by the original WannaCry authors.”
Ultimately, WannaCry should prove to be a relatively cheap warning shot. At the time of writing, only $50,000 has been transferred to the bitcoin wallets of the hackers. The U.S. Cyber Consequences Unit estimates that the total cost of the ransomware will top out in the range of the hundreds of millions of dollars and is unlikely to exceed $1 billion globally. It could have been a lot worse (and it is not even the first case of a state-developed cyber weapon going awry – many cyber weapons have a propensity for unintended contagion; even the painstakingly constructed Stuxnet worm inadvertently spread to computers in 155 countries). There also have not yet been any reports of human injuries or deaths as a result of WannaCry. However, given the cyber vulnerabilities of airplanes, cars, and nuclear power plants, were a group of murderous (instead of merely greedy) hackers to have used a more destructive piece of malware from the NSA cyber arsenal that was up for sale there could have been a devastating number of global fatalities.
So what to do about secret, highly funded weapons programs around the world that have developed tools that if they fall into the wrong hands could potentially cause uncontrollable global destruction? Fortunately, the world has faced a similar problem before. Concerned about the possible unleashing of a global contagion through modern biological weapons, the world’s states settled upon the Biological Weapons Convention in 1972, which banned the “development, production, and stockpiling” of biological weapons. The development of the remarkably successful convention has given states valuable experience in banning an entire class of weapons, treaty compliance, and fostering of a global shared norm.
The world would benefit from its cyber equivalent. Since the Geneva Conventions, it has been a widely accepted convention of warfare that the use of weapons has to discriminate between military and civilian targets and be proportionate to the threat at hand. Like biological weapons, cyber weapons are potentially both uncontrollably indiscriminate and disproportionately destructive meaning that their users risk committing war crimes. Such cyber spreading can be merely inconvenient or even harmless, but when coupled with the to date unknown maximum destructiveness of cyber weapons the results could be catastrophic.
These pre-existing norms of warfare have been relatively successful in restraining states from using their most destructive cyber weapons. During opportunities during the 2003 U.S.-led invasion of Iraq, the 2008 Russian incursion into Georgia, and the 2011 NATO intervention in Libya, as well as the 2016 coalition engagement of ISIS, states have refrained from using their most destructive cyber weapons. Although setting precedents, revealing capability, concerns over boomerang blowback, and limited utility in target-poor environments also have played a role in discouraging the use of cyber weapons in the past, an overriding concern in almost every case has been unanticipated collateral damage, particularly with hospitals. In light of last year’s international reaction to the U.S. accidentally attacking a single hospital in Afghanistan, it is easy to see why states are hesitant to use weapons that could harm hundreds or thousands of them.
However, non-state actors such as the Shadow Brokers (or whoever they sold the NSA ransomware to) are not bound by the same norms or held to the same standards. As the WannaCry episode clearly demonstrates, such groups have no compunction about using cyber tools to attack hospitals, schools, or other generally considered out-of-bounds targets. These groups either do not know how to narrowly target these carefully calibrated weapons or more likely do not care. The combination of this lackadaisical attitude with the easy availability of the world’s most destructive code either for free or for auction should prompt deep introspection about cyber weapons development and protection. Russia and Microsoft have already publicly criticized the stockpiling of the cyber vulnerabilities that made WannaCry possible. The world was lucky this time, but if it does not take action soon, it may rue the day that it did not take the necessary steps to protect itself from the powerful cyber weapons that it has developed.
Patrick Cirenza has written two theses on cyber warfare and cyber espionage and has publications on the topics in the Bulletin of the Atomic Scientist, Slate Magazine, the Royal United Services Institute Publications, and Nations & States. He is currently a presidential management finalist.