Twenty years ago, I testified before a U.S. congressional committee on China’s espionage operations in the United States. I left the Members with what I thought was an ominous warning: “Do something about this now or you’ll be calling me back in 20 years screaming: ‘My God, how did this happen?’ ” Well, they never called me back, but if recent FBI arrests are any indication, the problem has gotten worse — a lot worse.
On October 30, 2018 the U.S. Department of Justice announced the indictment of 10 Chinese intelligence officers and cyber hackers from the Ministry of State Security (MSS), China’s main civilian espionage organization. The United States charged the group with stealing airline engine technology from French and U.S. companies. The alleged scheme ran from 2010 to 2015 and targeted turbofan engine technology developed through a U.S.-French partnership. The objective of this espionage was to steal intellectual data and confidential business information about the engine. China’s defense industry is working to develop a comparable engine.
Weeks earlier, on October 10, the FBI announced the arrest of Mr. Yanjun Xu, alleged deputy division director of the Jiangsu Province Office (sixth bureau) of the Ministry of State Security, China’s main civilian spy agency. The FBI’s affidavit describes luring Xu to Belgium to illegally purchase General Electric commercial aviation technology. Belgian authorities placed him in custody on arrival and put him on a plane to the United States (most likely with an FBI escort). It is probably not a coincidence that FBI also arrested Mr. Chaoqun Ji, a PRC national in Chicago, on espionage related charges. The FBI indictment alleges Ji was tasked by his spymaster — a senior MSS officer in the Jiangsu Province MSS office.
For the United States, the problem is not these recent cases. Nations have been spying on the United States (and us on them) since the American Revolution. The problem is that these recent indictments and arrests are only two of hundreds, if not thousands of cases. These activities support a national concerted effort to expand China’s economic and security interests. Most of China’s espionage activities are not “traditional espionage,” yet they are having a profound impact on America’s economic wellbeing, national security, and potentially our political and governance processes. U.S. intelligence, security, and law enforcement apparatus is just starting, 20 years later, to catch on.
Key Highlights
This report presents initial findings from analysis of 274 documented cases of Chinese worldwide espionage since the year 2000. High-level findings are as follows:
- China has expanded its espionage efforts considerably over the last 20 years.
- Chinese entities conducting espionage include government agencies, the military, state- owned enterprises (SOEs), private companies/individuals, and select universities.
- Nearly half of China’s espionage efforts target U.S. military and space technologies. Almost 25 percent of cases target commercial interests.
- China is unlikely to significantly curb its espionage efforts, as they provide a cost-efficient means to expand the economy, advance research and development, project military power, and meet China’s stated goal to become a world power.
Types of Chinese Espionage
One cannot simply look at a single or even several espionage cases and hope to understand if, and how, a nation state is conducting espionage. That type of understanding takes evidence based off detailed analysis of a sufficient body of data. Over the last five years, I compiled and analyzed 274 cases of Chinese espionage that have occurred since the year 2000. Detailed analysis of these cases provides ample evidence that China is conducting espionage, as well who is responsible, their information objectives, gaps in their knowledge, and operational “tradecraft” techniques.
There is a wide variance in what the media, public, and U.S. legal codes define as “espionage.” Four U.S. statutes and administrative regulations encompass those definitions:
- Traditional espionage (18 USC 792-799): The practice of spying or using spies to obtain information about the plans and activities of a foreign government.
- Economic Espionage Act of 1996: The theft of trade secrets that includes the intent to benefit a foreign entity or at least know that the offense will have that result.
- Illegal Exports: Export Administrative Regulations (EAR) deals with the illegal export of sensitive dual use technology and International Traffic in Arms Regulations (ITAR) with the more serious act of illegally exporting Munitions List armaments/technology and Missile Technology Control Regime and technology.)
- Covert Action, or Foreign Agents Registration Act (18 USC 951): FARA passed in 1938 and requires that agents representing the interests of foreign powers in a “political or quasi-political capacity” must disclose their relationship with the foreign government and information about their activities and finances. Covert Action is carrying out these activities without disclosure and is intended to create a political effect and conceal the identity of, or allow plausible denial by, the sponsor.
For the purposes of this study, all the aforementioned legal definitions of criminal acts are categorized as “espionage.” This espionage definition considers media and common public usage, and similarities in the acts, i.e. conducting illegal covert or clandestine acts at the direction of, or for the benefit of, a foreign government or entity. When divided into the aforementioned categories (Espionage, Economic Espionage, ITAR, EAR, Covert Action) the 274 espionage cases show the percentages of operations as follows (Figure 1.).
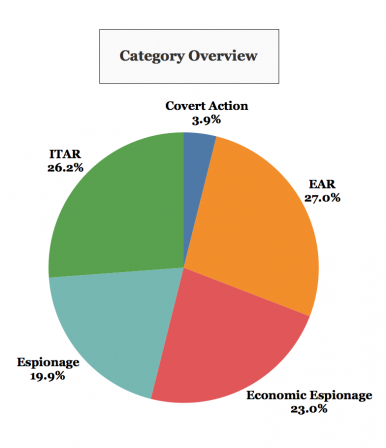
Figure 1: Categories of Chinese Espionage.
Chinese Espionage Entities
Espionage activities correlated to their sponsoring organization (the “customer” receiving the information or technology) showed four distinct clusters of Chinese organizations engaging in espionage. The governing Chinese Communist Party (CCP) uses government, quasi-government, academic, and commercial entities as mechanisms to conduct all forms f espionage abroad.
China’s preeminent civilian intelligence agency is the Guojia Anquan Bu, or Ministry of State Security (MSS). The MSS was formed in June 1983 by combining the espionage, counterintelligence, and security functions of the Ministry of Public Security and the Investigations Department of the Chinese Communist Party Central Committee.
On the military side, the People’s Liberation Army (PLA) General Staff Headquarters, Second Department is responsible for collecting military information, including related foreign technology. PLA collection capabilities include military attachés conducting overt and clandestine collection and collectors under other government and commercial covers.
State-owned enterprises are also engaged in espionage. There are 150,000 SOEs in China, 50,000 of which are owned by the central government and include aerospace and defense companies, research institutes, technology transfer organizations. The central government directly manages 102 of these firms considered critical to national and economic security. The CCP’s Organization Department makes all senior personnel appointments within these business organizations. CCP embedded committees manage all actions within directly managed SOEs. In 2018, CCP leader and Chinese President Xi Jinping directed all SOEs to amend their bylaws to ensure the concepts of service to the CCP as well as national and economic security are placed above profit.
In approximately 60 cases I reviewed, Chinese companies or individuals were acting unilaterally for commercial benefit only. In some of those cases (perhaps 20 percent), there was a clearly identifiable Chinese government or SOE as the ultimate customer for illegal exports or trade secrets. This was often the case in illegal export of military technology, source code, large-scale agricultural and industrial production and manufacturing techniques.
Other Chinese government elements that collect intelligence (information) include the PLA Political Department Liaison Office (targeted against Taiwan), United Front Work Department, and the Ministry of Industry and Information Technology.
China-Based “Customers” Conducting Espionage Activities
The distribution of Chinese espionage cases worldwide illustrates the magnitude of CCP controlled businesses, research entities, and government organizations involved in espionage activities (see Figure 2). There is a near equal distribution of espionage activities between the four major organizational clusters. This distribution indicates a concerted effort to use all mechanisms of government and the economy to collection foreign information and technology. Beijing has stated its intention to advance industry, technology, and military capabilities to become a world leader by 2025. At a minimum, there is no indication that the CCP or Chinese government have taken any measures to impede the illegal activities (illegal in the United States) of their state corporations and citizens.
The statistics show Chinese private companies adopt an aggressive posture in conducting economic espionage activities, resulting in 60 cases prosecuted just in the United States. Similarly, SOEs are aggressive in conducting or supporting espionage (72 acts total), stealing primarily advanced military technology. Espionage activities involving the People’s Liberation Army reflect primarily illegal arms or military technology transfers where the PLA was known, or believed to be the end user – for example, the PLA was assumed the ultimate end user or “customer” if a TOW anti-tank system (tube-launched, optically tracked, wireless-guided weapon system) was being illegally shipped to China. The PLA was involved in 61 such cases.
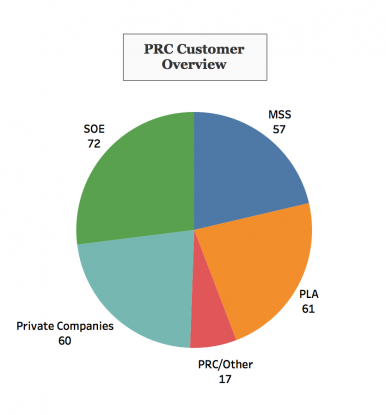
Figure 2: Chinese Organizational Clusters Committing Espionage.
Distribution of Chinese Espionage Activities in the U.S.
China’s main espionage activities against the United States are focused on the illegal export of military and dual use technology. Together, they make up 54 percent of cases. Economic espionage, which is mainly conducted by private companies or individuals, makes up 23.5 percent of cases. The category of “traditional espionage” can be seen at 18 percent; but is considerably lower when Taiwan is removed as a PRC intelligence target. The venues for prosecution show where the target company or organization was located (see Figure 3.) The distribution pattern shows activity concentrations occurring in high-tech sectors, manufacturing hubs, and business centers. Victims of China’s espionage efforts include major defense and aerospace companies, pharmaceutical firms, technology research companies, manufacturers, and universities.
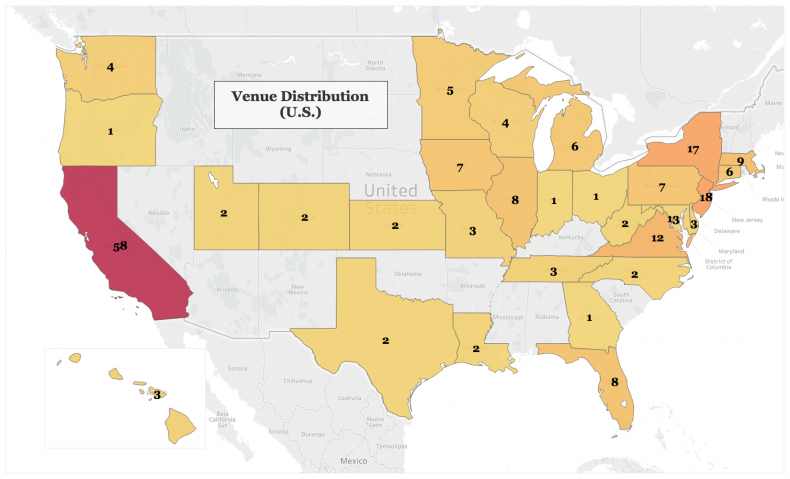
Figure 3: Distribution of Chinese Espionage Cases in the United States.
Intelligence Information Objectives
In intelligence terminology, information objectives identify the specific information (or technology) that is tasked for collection. These can number in the thousands and reflect the organization’s knowledge gaps. Simply put, if a country is continually trying to collect information on specific components of the F-35 aircraft, it is because it lacks the required information for its planned purposes.
China’s information objectives are focused in priority sectors and technologies. The Director of National Intelligence report, Foreign Economic Espionage in Cyberspace (2018) identifies key industries and technologies that are frequent targets of foreign espionage. The text in bold (see Figure 4) reflects multiple, concerted attempts by China to secure specific U.S. critical technologies. Each of these technologies is identified as a priority requirement in China’s State Council 2015 strategic plan “Made in China 2025.”
More than 60 percent of China’s attempts to illegally export U.S. critical technologies are targeted at military technologies or space systems. These information objectives include systems, designs, components, radiation hardened chips, integrated circuits, software, manuals, precision optics, thermal imaging systems, production techniques, etc.
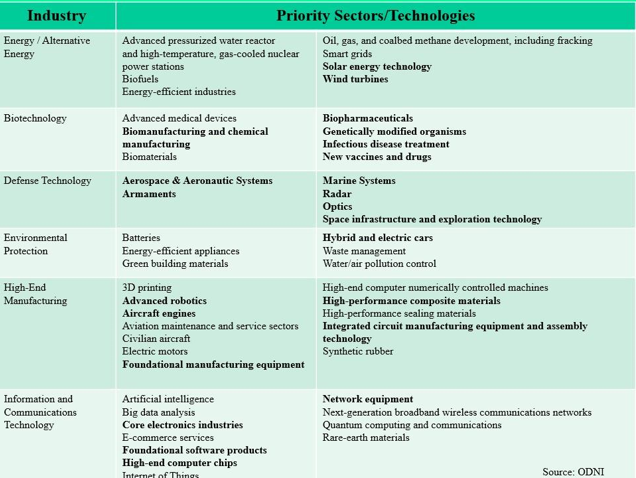
Figure 4: Adapted from Office of the Director of National Intelligence,
Espionage Tradecraft
The final aspects of Chinese espionage activities are their use of specific clandestine collection techniques commonly known as espionage “tradecraft.” Chinese government agencies, SOEs, companies and individuals employ varying levels of sophistication of espionage tradecraft. An analysis of operational activities reveals a wide range of tradecraft practices (see Figure 5):
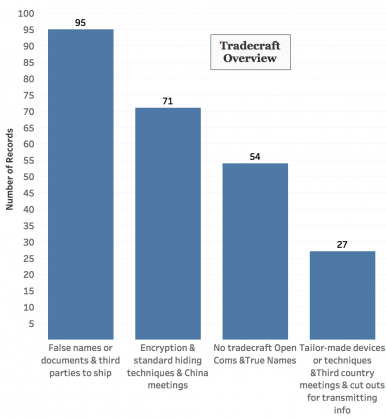
Figure 5: Tradecraft Overview.
- No tradecraft, with parties using open communications and true names;
- Use of false names and/or third parties to transmit information and ship materials; Public and commercial encryption, hosting meetings in China to avoid detection; Tailor made devices or techniques, use of third countries, use of in-country cutouts to transmit information.
As illustrated, the most frequently employed elements of tradecraft include using false names or documents to ship information or technology. These techniques were used approximately one-third of the time. In nearly 25 percent of cases, individuals employed encryption for communications and/or hosted meetings in China to avoid detection by U.S. law enforcement. In 54 cases, entities used no tradecraft or substantive attempts to hide the espionage activity. Individuals used true names and open communications including emails, text messages, and phone calls. Lastly, in 27 cases, roughly 9 percent of the total, case officers and/or agents displayed a more sophisticated level of tradecraft. These elements of tradecraft included specially designed smartphone software for secure covert communications (U.S. vs. Kevin Mallory); third country meetings, or use of third parties (cutouts) in the United States for communicating information between the in-country ‘handler” and recruited asset, or the in-country handler and Chinese intelligence services.
Tradecraft Islands of Excellence
The wide variance in sophistication of espionage tradecraft implies the idea of “Islands of Excellence” (see Figure 6) — meaning China employs espionage tradecraft with varying degrees of sophistication and effectiveness. One might expect poor tradecraft from nonprofessional intelligence entities such as individuals, companies, and SOEs. However, cases attributed to the Ministry of State Security show an astounding nine cases where case officers and recruited agents demonstrated no discernible tradecraft. In these cases, persons conducted agent recruitment, tasking, communications, and data transfer openly, with no significant attempt to hide the activity. In another 22 cases, MSS operatives employed only simplistic or limited operational tradecraft. In only eight cases was there a sophisticated higher level of tradecraft employed.
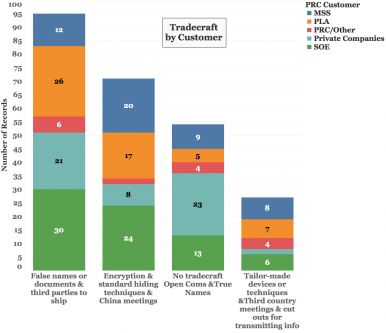
Figure 6: Espionage Tradecraft Techniques by Specific PRC Entities.
This wide variance in professional tradecraft likely indicates MSS suffers from lack of standardized training, security awareness, operational oversight, and case management. In addition, the same erratic performance by recruited agents illustrates nonstandardized agent training, protocols, and practices. The poor performance in oversight and case management is possibly due to the highly politicized nature (CCP management) of Chinese intelligence. If this is in fact the case then MSS performance is not likely to improve anytime soon.
Analysis reveals several other interesting data points on the application of tradecraft. Private companies (and individuals) are most likely to employ no or minimal tradecraft. In these cases no (23 cases) or minimal tradecraft (21 cases) was employed. The minimal application of tradecraft is expected, as these cases typically do not involve professional intelligence operatives (either case officers or agents).
SOE espionage activities show a wide variance in tradecraft. The operational details revealed in individual cases implies this phenomenon is due to the following factors: no training program for handlers or recruited assets, differences in the various SOEs, and the variables of espionage targets to include military, space, dual use, or industrial technologies.
Conclusion
Several high-level conclusions can be drawn from the cases representing the last 20 years of Chinese espionage operations. Espionage operations have expanded dramatically, increasing in the number of operations, personnel, government and SOE’s, and foreign targets sets. There is also a national construct in place (however redundant) to ensure intelligence information objectives are satisfied by collecting foreign information and technology. These information objectives are also tied to national defense and economic priorities. The only notable area in which China has shown minimal advancement has been in applying sophisticated espionage tradecraft. Lastly, China’s espionage activities continue unabated despite a large number of arrests, public exposure, and most recently, U.S. trade sanctions.
Nicholas Eftimiades is a lecturer at Penn State University, Homeland Security Program. He recently retired from a 34 year government career that included employment in the CIA, Department of State, and Defense Intelligence Agency. The views in this article are the author’s own and do not reflect the views of the U.S. government.
































